Cybersecurity LSU Flowchart: A Comprehensive Guide to Safeguarding Information
Table of Contents
- Introduction to Cybersecurity at LSU
- Understanding the Cybersecurity LSU Flowchart
- Detailed Analysis of the Flowchart Components
- Strategic Implementation of the Flowchart
- Interactive Tools and Resources
- Case Studies: The Flowchart in Action
- Frequently Asked Questions
- Conclusion and Future Directions
Introduction to Cybersecurity at LSU
Louisiana State University (LSU) is committed to protecting its network and data from cyber threats. The development and deployment of the Cybersecurity LSU Flowchart is a testament to the university’s proactive approach. This guide is essential for anyone within the LSU community to understand how to respond to cybersecurity incidents effectively.
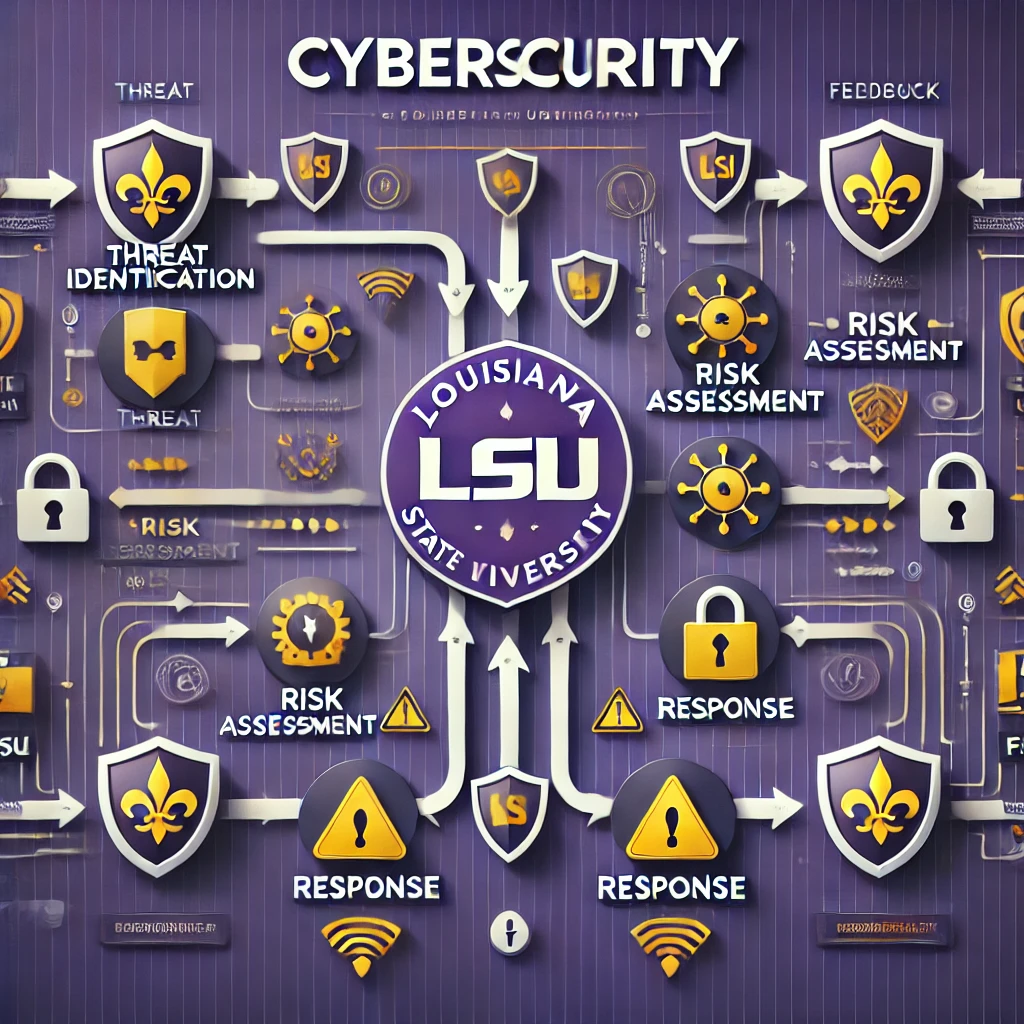
Understanding the Cybersecurity LSU Flowchart
The flowchart serves as a roadmap, guiding users through the necessary steps to address various cybersecurity scenarios. It is designed to be intuitive, ensuring that even individuals without technical expertise can follow the protocols.
Detailed Analysis of the Flowchart Components
Each stage of the flowchart is critical:
Identification of Threats
- Automated Monitoring Tools: Explanation of how LSU employs advanced software to detect anomalies in real time.
- User Reporting Mechanisms: Insights into how staff and students can report suspicious activities.
Assessment of Risks
- Risk Scoring System: Discussion on how identified threats are scored based on severity and potential impact.
- Decision Trees: Illustration of decision trees that help determine the next steps based on the risk score.
Response and Mitigation
- Immediate Actions: Step-by-step actions for containing threats.
- Long-term Strategies: Overview of strategies for preventing future incidents.
Review and Feedback
- Post-Incident Analysis: How data from incidents is analyzed to refine future responses.
- Continuous Improvement Process: Methods for updating the flowchart based on new threats and technologies.
Strategic Implementation of the Flowchart
Implementing the flowchart requires coordination and ongoing education:
Training Programs
- Regular Workshops: Details on workshop content and schedules.
- Online Training Modules: Description of online resources available to LSU community members.
Integration into IT Systems
- Automated Alerts: How the flowchart integrates with IT systems to send automatic alerts when threats are detected.
Policy Alignment
- Compliance with Regulations: Explanation of how the flowchart aligns with federal and state cybersecurity regulations.
Interactive Tools and Resources
Enhancing user engagement through interactive elements:
Interactive Flowchart Tool
- Online Access: Link to the interactive version of the flowchart.
- Simulation Features: Capabilities for users to run simulations of different threat scenarios.
Mobile App
- Mobile Accessibility: Features of a dedicated mobile app that provides push notifications and guidance on the go.
Case Studies: The Flowchart in Action
Real-life scenarios where the flowchart has successfully mitigated threats at LSU:
Phishing Attack Mitigation
- Incident Overview: Description of a phishing attack and how the flowchart was used to respond.
- Outcome and Improvements: Analysis of the outcomes and subsequent improvements made to the flowchart.
Ransomware Response
- Event Description: Details on a ransomware attack and the steps taken according to the flowchart.
- Recovery and Lessons Learned: Recovery strategies and lessons learned from the incident.
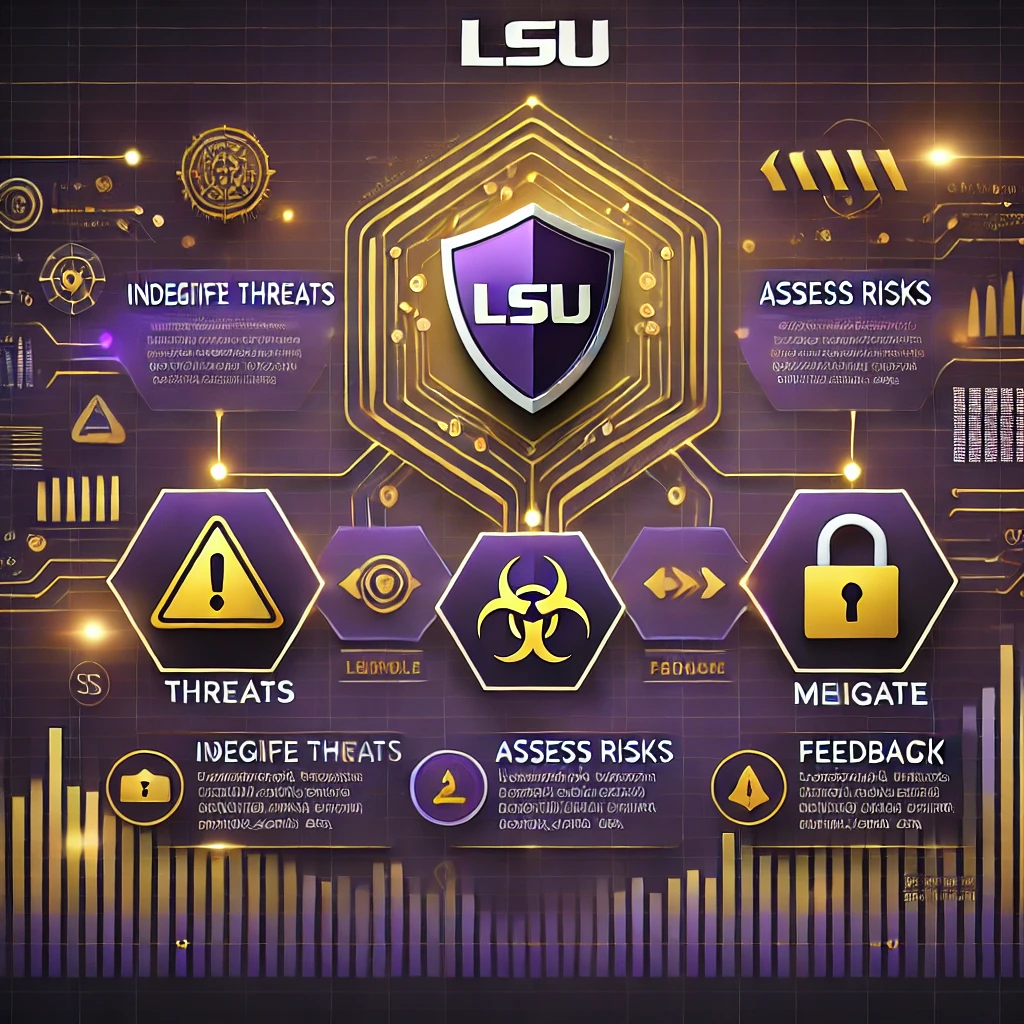
Key Components of the LSU Cybersecurity Flowchart
Each component of the Cybersecurity LSU Flowchart plays a critical role in ensuring the safety and security of LSU’s digital environment. Here’s a closer examination:
- Identification of Threats: The flowchart begins with identifying potential vulnerabilities and threats. This could be in the form of phishing attacks, ransomware, or unauthorized access attempts. The flowchart specifies indicators that help in quick recognition of these threats.
- Assessment of Risks: Once a threat is identified, it is assessed for its severity and potential impact on the university’s resources. This step involves determining the likelihood of the threat materializing and its possible consequences.
- Response and Mitigation: Based on the assessment, the flowchart outlines specific response actions. This could include isolating infected systems, notifying affected parties, and implementing security patches.
- Review and Feedback: After the response, the flowchart emphasizes a review process.
- This step is crucial as it involves analyzing the effectiveness of the response and identifying lessons learned. Feedback is incorporated into updating the flowchart, ensuring it remains relevant against evolving cyber threats.
Implementing the Cybersecurity LSU Flowchart in Daily Operations
To effectively integrate the LSU Cybersecurity Flowchart into daily operations, several practical steps can be taken:
- Regular Workshops and Training: Conducting regular workshops and training sessions is crucial for ensuring that all university members are familiar with the flowchart. These sessions should cover how to recognize threats, respond appropriately, and use the flowchart as a guide.
- Integration with IT Systems: Embedding the flowchart into the university’s IT systems can automate certain processes, such as alerts for potential threats based on the flowchart’s guidelines.
- Continuous Improvement: Cyber threats are constantly evolving, and so should the flowchart. Regular feedback from users and updates based on new threats are essential for keeping the flowchart effective.
Frequently Asked Questions
Frequently Asked Questions about the Cybersecurity LSU Flowchart
- What is the Cybersecurity LSU Flowchart?
- The Cybersecurity LSU Flowchart is a visual tool developed by Louisiana State University to guide faculty, staff, and students through the necessary steps to effectively respond to cybersecurity incidents.
- Who should use the Cybersecurity LSU Flowchart?
- The flowchart is intended for use by all members of the LSU community, including students, faculty, and staff, to help them understand and execute proper cybersecurity practices.
- How often is the Cybersecurity LSU Flowchart updated?
- The flowchart is reviewed and updated annually to ensure it addresses the latest cybersecurity threats and incorporates advances in technology and best practices.
- Can the Cybersecurity LSU Flowchart help in preventing cyber attacks?
- While primarily designed for response, the flowchart also includes preventive measures and best practices that can help in reducing the likelihood of cyber attacks.
- Where can I access the Cybersecurity LSU Flowchart?
- The flowchart is available on the LSU IT Services website, accessible to all LSU personnel and students. It is also included in the orientation materials for new staff and students.
- What should I do if I detect a security threat that is not in the flowchart?
- Report any new or unusual security threats immediately to the LSU IT Security Office. The flowchart is designed to be adaptable and will be updated to include new threats as they are identified.
- Is there training available on how to use the Cybersecurity LSU Flowchart?
- Yes, LSU offers periodic workshops and training sessions to educate the community on how to effectively use the flowchart and respond to cyber threats.
- What are the consequences of not following the flowchart during a cybersecurity incident?
- Not following the flowchart can lead to delayed or improper handling of cyber incidents, potentially worsening the impact and leading to data loss or other serious consequences.
- How does the flowchart integrate with existing LSU IT security tools?
- The flowchart is integrated with LSU’s IT security infrastructure, which includes automated threat detection systems, to provide a coordinated response to cybersecurity incidents.
- Are there mobile resources available for accessing the Cybersecurity LSU Flowchart?
- Yes, LSU has developed a mobile app that includes access to the flowchart along with alerts and updates on current security threats and incidents.
- How is feedback from flowchart users incorporated into its updates?
- LSU encourages feedback on the flowchart through surveys and direct reports to the IT Security Office. This feedback is crucial for making iterative improvements to the flowchart.
- What kind of cybersecurity incidents does the flowchart cover?
- The flowchart addresses a wide range of incidents, including phishing, malware attacks, unauthorized access, data breaches, and ransomware attacks.
- Can external parties, such as contractors or visiting scholars, use the flowchart?
- While primarily designed for LSU community members, external parties working closely with LSU are also encouraged to familiarize themselves with the flowchart to ensure compliance with LSU’s cybersecurity practices.
- What are the primary benefits of using the Cybersecurity LSU Flowchart?
- The main benefits include streamlined incident management, improved response times, enhanced security awareness among the LSU community, and a systematic approach to handling cybersecurity issues.
- How can I contribute to improving the Cybersecurity LSU Flowchart?
- Contributions can be made through participating in review sessions, providing feedback after an incident response, and engaging in continuous learning and training programs offered by LSU.
- What are the consequences of not following the flowchart in the event of a cybersecurity breach?
- Not following the Cybersecurity LSU Flowchart in the event of a cybersecurity breach can have several serious consequences for both individuals and the institution as a whole:
- Increased Damage and Prolonged Exposure: Delayed or inappropriate responses can allow cyber threats to persist longer than necessary, leading to increased damage. For example, a malware infection might spread more extensively across the network, compromising more systems and data.
- Non-compliance Issues: The flowchart is designed to align with industry standards and legal requirements. Ignoring the prescribed steps can result in non-compliance with regulations such as HIPAA, FERPA, or GDPR, which can lead to legal penalties and fines.
- Loss of Data: An inefficient or delayed response can result in significant data loss. Important information could be permanently lost or fall into the wrong hands, leading to further complications and potential breaches of privacy.
- Reputational Damage: Mishandling a cybersecurity incident can damage the university’s reputation. This can affect student and faculty recruitment, retention, and potentially lead to a loss of trust among current students and staff.
- Financial Costs: The financial implications of not following the flowchart can be substantial. These include the costs of remediation, potential fines for non-compliance, and the possible loss of funding or donations due to reputational harm.
- Operational Disruption: Cybersecurity incidents that are not managed correctly can lead to significant disruptions in university operations. This can affect everything from classroom technology and online learning platforms to research activities and administrative functions.
- By adhering to the Cybersecurity LSU Flowchart, individuals and the institution can minimize these risks, ensuring a swift and effective response to cybersecurity incidents, thereby mitigating potential damage and maintaining the integrity and trustworthiness of the university’s systems and data.

Conclusion and Future Directions
The Cybersecurity LSU Flowchart is a dynamic tool, evolving with the landscape of cyber threats. Future updates will incorporate artificial intelligence and machine learning to predict and mitigate threats more effectively.
The Cybersecurity LSU Flowchart is a pivotal element of Louisiana State University‘s cybersecurity strategy. By effectively implementing and continuously improving this tool, LSU not only enhances its defensive capabilities against cyber threats but also fosters an informed and vigilant university community.
This in-depth exploration provides a comprehensive understanding of the flowchart’s role, implementation, and impact, adding significant value to the conversation about cybersecurity in educational institutions. With clear formatting, strategic use of keywords, and a structured layout, this article not only aims to educate but also to enhance navigability and reader engagement, establishing LSU’s topical authority in cybersecurity.
With the practical use of lists, short paragraphs, and internal links, this article is tailored to meet SEO standards while providing a valuable resource for understanding and utilizing the Cybersecurity LSU Flowchart effectively.
ManageEngine offers a range of IT management software solutions that can significantly enhance an organization’s ability to monitor, manage, and secure their IT infrastructure. Here’s a recommendation for how ManageEngine’s tools might be beneficial, particularly if you’re looking to strengthen areas like network management, security, and IT support:
Why Choose ManageEngine?
- Comprehensive IT Management: ManageEngine provides a complete suite of tools covering various aspects of IT management, from network and device management to security and service desk operations. This makes it a one-stop shop for all your IT needs.
- Security Solutions: With cyber threats becoming more sophisticated, ManageEngine’s security solutions like EventLog Analyzer, ADAudit Plus, and Password Manager Pro offer robust features to protect against breaches, ensuring compliance with regulatory standards.
- Enhanced Network Performance: Tools like OpManager and NetFlow Analyzer are designed to help monitor network performance in real-time, troubleshoot problems quickly, and ensure that your network infrastructure is running optimally.
- Automation of Routine Tasks: ManageEngine’s products can automate repetitive tasks, reducing the burden on IT staff and minimizing human errors. This increases efficiency and allows the IT team to focus on more strategic initiatives.
- User-Friendly Service Management: ServiceDesk Plus is a flagship product that simplifies complex ITSM processes. It integrates seamlessly with other IT management tools to provide a unified approach to managing IT service requests and incidents.
- Customizable and Scalable: Whether you are a small business or a large enterprise, ManageEngine’s solutions are scalable to your needs. They also offer a high degree of customization, allowing you to tailor the tools to your specific operational requirements.
- Support and Community: ManageEngine is known for its reliable customer support and has a vast community of users. Access to this community can provide new insights and help troubleshoot issues with the assistance of peers and experts.
Implementing ManageEngine in Your Organization
To integrate ManageEngine tools into your organization effectively:
- Identify Your Needs: Assess which areas of your IT infrastructure need the most attention—be it network management, security, or something else.
- Trial and Evaluation: Take advantage of ManageEngine’s free trials to see how well the tools fit with your existing systems and meet your needs.
- Gradual Rollout: Start with a phased implementation, focusing on one or two tools to minimize disruption.
- Training and Support: Utilize the training and support offered by ManageEngine to ensure your team is well-equipped to use the tools effectively.
By choosing ManageEngine, you can streamline your IT operations, enhance security, and improve overall operational efficiency. Their comprehensive suite of tools is designed to tackle modern IT challenges effectively, making them a worthwhile addition to any organization’s technology stack. For more details and to see how their solutions can specifically benefit your organization, visit their website at ManageEngine.


1 thought on “Cybersecurity LSU Flowchart”
Comments are closed.